How does Claude access
your internal APIs?
Internal APIs require client certificates. Zero-trust networks need proof of identity. The Cyphers HTTPS MCP Server gives Claude the credentials to access enterprise systems.
Unlock enterprise connectivity for Claude.
Claude Code is powerful. But connecting to internal APIs, zero-trust networks, and regulated systems often requires security controls beyond standard HTTPS. Claude HTTPS bridges that gap—giving your AI assistant the credentials to operate in enterprise environments.
Connect to Zero-Trust APIs
Many internal services require mutual TLS authentication. Claude HTTPS adds client certificate support so Claude can access APIs that demand cryptographic identity.
Meet Compliance Requirements
FIPS 140-3, certificate pinning, revocation checking. When your security policy has specific transport requirements, Claude HTTPS delivers them.
Keep Control Centralised
One JSON config file governs all TLS behaviour. No per-request configuration. No scattered settings. Security teams get visibility and control.
mode: "FIPS_STRICT",
mtls: {
cert: env.CLIENT_CERT,
key: env.CLIENT_KEY
},
pinning: ["sha256/...", "sha256/..."]
};
One Config File. Complete Control.
Configure at ~/.claude/https-config.json. All TLS behaviour governed from a single location.
Install in 60 Seconds
Add hardened TLS to Claude with a single command.
Zero-install option
Don't want to install globally? Use npx to run directly:
The -y flag auto-confirms the install prompt. Claude Code will fetch the latest version each time.
From Prototype to Production
Everything you need to ship with confidence.
FIPS 140-3 Cryptography
Built on a validated cryptographic module. Ensures all data in transit meets federal security requirements for classified and sensitive workloads.
First-Class mTLS
Configure client certificates directly in JSON or reference them from secure storage. PKCS#12 and PEM formats both supported natively.
Certificate Pinning
Prevent Man-in-the-Middle attacks by pinning server certificates or public keys. Supports leaf, intermediate, root, and SPKI hash pinning.
Custom CA Bundles
Trust private internal Certificate Authorities alongside or instead of public roots. Bundled Mozilla NSS CA bundle included.
Revocation Checking
Perform real-time OCSP and CRL checks to ensure server certificates haven't been revoked. Configurable soft or hard fail modes.
Detailed Auditing
Log every handshake detail, cipher negotiation, and validation failure. Export to SIEM in JSON, CEF, or Syslog format.
Built For
Financial Services
Connect Claude to trading APIs, payment gateways, and internal systems that require mTLS and strict cipher policies.
Healthcare & Life Sciences
Access HIPAA-compliant services with certificate pinning and full audit trails for every request.
Government & Defence
FIPS 140-3 mode ensures Claude meets federal cryptographic requirements for sensitive workloads.
Enterprise IT
Let developers use Claude while maintaining centralised control over transport security policies.
Free vs Pro
Same security. Different scale.
Free
Get started with Server Authenticated TLS (HTTPS) + mTLS
- Server Authenticated TLS (HTTPS) (TLS 1.3, Authenticated Encryption with Associated Data (AEAD))
- mTLS with 5 client certificates
- 2 server certificates
- Bundled Mozilla CA Bundle
- Custom CA Paths
- Cyphers Hub access
Pro
Scale + compliance for production
Everything in Free, plus:
- Unlimited client certificates
- Unlimited server certificates
- FIPS 140-3 mode
- Certificate pinning
- Hard-fail revocation
- SIEM export (JSON, CEF, Syslog)
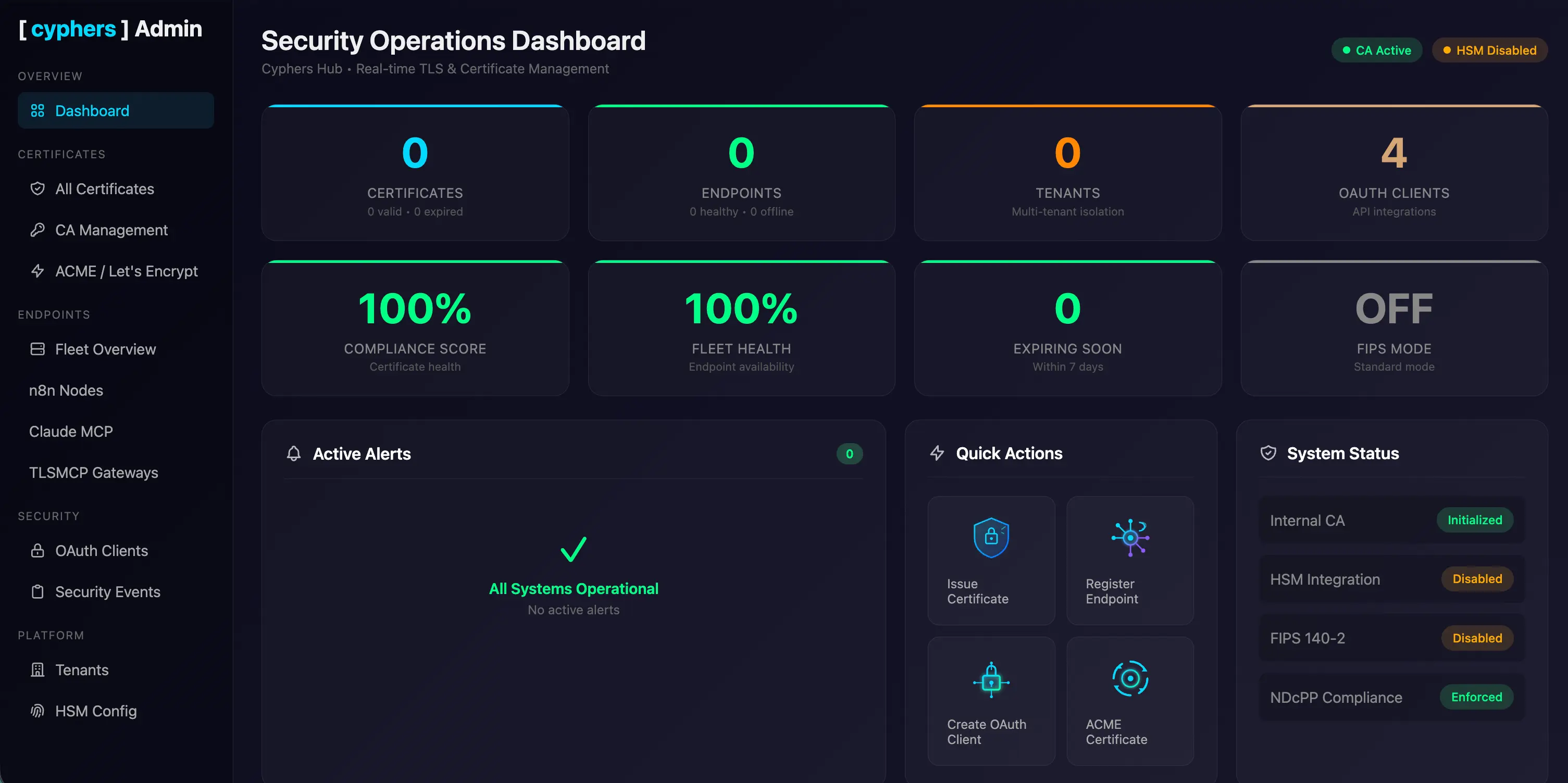
Visibility into what your systems are doing.
Developers build integrations and automations fast. Cyphers Hub gives security teams a single dashboard to monitor the systems they create—TLS policies, certificate status, and connection health across every deployment.
- Centralised policy enforcement across all systems
- Certificate expiration alerts before outages happen
- Configuration drift detection
- Audit-ready compliance reports
Give Claude access to your internal APIs.
5 minutes to set up. Free tier includes Server Authenticated TLS (HTTPS) + 5 client certificates.